Fortifying Your Crypto Transactions: Introducing Advanced Address Poisoning Detection
We're excited to announce a significant upgrade to our API, now featuring cutting-edge address poisoning detection powered by Trugard's innovative engine. As address poisoning becomes a more common and costly scam, our latest enhancement offers a robust, intelligent defense that integrates seamlessly into your existing workflows.
What is Address Poisoning?
Address poisoning is a deceptive tactic used by scammers to trick users into sending funds to a malicious address that visually mimics a legitimate one. Here’s how it typically works:
- Target Identification Attackers scan the blockchain for wallets with significant activity.
- Crafting a Lookalike They generate a wallet address that closely resembles the target (same prefix or suffix).
- Sending a Tiny Transaction A small amount of valueless token (e.g., 0.00001 ETH) is sent from the spoofed address to the target wallet.
- Polluting Transaction History This fake transaction now appears in the victim’s history, where they might later copy it thinking it's a legitimate address.
- Funds Lost When users unknowingly send funds to this fake address, they’re permanently lost.
Real-World Examples
- ✅ Legitimate Huobi Address 0xdf574c24545e5ffecb9a659c229253d4111d87e1
- ⚠️ Spoofed Address 0xdf57e7d894945ed102f19a91aaf7e117901dea68
- ✅ Legitimate Binance: 0x2c11a3A5F725a21024DC5467f69eb649b1CD9C0b
- ⚠️ Spoofed: 0x2c1134A046C659fc9c3dFb663061E3E6C7989c0B
How We Detect Address Poisoning
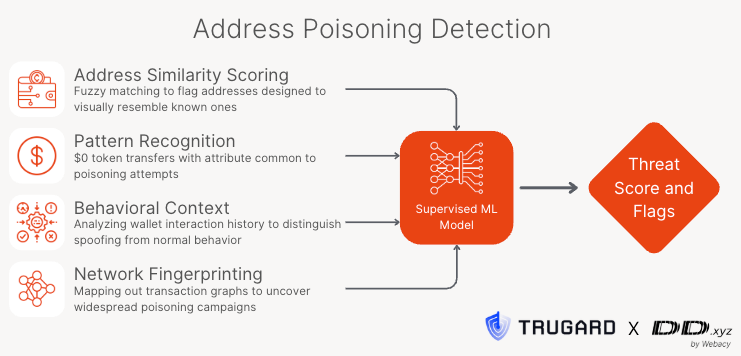
Trugard’s engine, integrated into DD.xyz endpoints, uses a multi-layered detection model built with XGBoost and enriched with behavioral and graph analytics.
Core Techniques Include:
- 🧬 Address Similarity Scoring: Fuzzy hashing + prefix/suffix matching to catch lookalikes.
- 📉 Zero-Value Transfer Patterns: Spotting $0 token transfers, a signature move in poisoning scams.
- ⏱️ Temporal Anomaly Detection: Looking for spoofed addresses that appear immediately after genuine ones.
- 🕸️ Graph Analysis: Mapping the relationships between addresses to uncover spam rings and coordinated campaigns.
- 🧠 Behavioral Fingerprinting: Comparing current transactions with historical wallet behavior to detect anomalies.
Together, these signals generate a threat score for each transaction, enabling real-time risk classification and alerts.
What Makes This Different?
Most systems rely on static blocklists or manual reviews. Our solution offers a distinct advantages:
- Proactive: Detects threats before funds are lost.
- Behaviorally Aware: Learns transaction patterns and adapts to new tactics.
- Continuously Learning: Our machine learning model constantly evolves and learns with emerging scams. Ensuring our detection capabilities and accuracy remain high and up to date.
- Collaborative by Design: Our APIs enable immediate alerts and interventions.
Built for Developers and Users:
- For Users: Seamless protection via Webacy and other partner integrations.
- For Developers: Plug-and-play APIs and threat feeds for wallets, explorers, and DeFi platforms.
Our enhanced address poisoning detection is primarily delivered through our API endpoints, allowing for flexible integration into a wide range of applications and platforms.
A Hybrid Security Model
- Proprietary Detection Engine: High-performance, closed-source model trained on live data.
- Open-Source Access: Many features are available for free via DD.xyz.
- Collaborative Threat Intelligence: We’re working toward decentralizing our threat DB to promote collaboration and transparency.
Why Now? The Threat is Growing
In late 2024, address poisoning surged. Bitcoin influencers like Jameson Lopp raised the alarm, and Chainalysis reported a spike in Ethereum incidents. Key drivers:
- Truncated address displays in wallets, increasing reliance on copy-pasting from transaction history.
- Near-zero gas fees on L2s enabling spam-scale attacks
- AI assistance for attackers generating convincing lookalikes
- Scammers impersonating trusted platforms (see Huobi and Binance samples above).
Poisoning will evolve. It will merge with phishing, wallet drainers, and impersonation scams. That's why we believe adaptive, intelligent defenses are not optional, they’re essential.
We’re here to help secure the future of Web3.