From the CTO’s Desk — September 2025 Address-Poisoning Results Analysis
Address poisoning has emerged as a leading threat in 2025. In September, wallet address books became a minefield. We catalogued address poisoning events all month across multiple EVM Chains from our XGBoost Model detection system and the losses are in the multi-millions. Here are some of the key findings:
🧩 TL;DR — September 2025
We detected 32,290 suspicious address-poisoning events affecting 6,516 unique victims during September 2025 (multi-chain).
Ethereum accounted for the vast majority of events (~91%), followed by Polygon (~6.7%) and Base (~1.9%).
Attackers overwhelmingly target stablecoins, USDT and USDC dominate exposure (see table and analysis below).
Key monthly statistics
- Total flagged poisoning events (September): 32,290.
- Unique victims: 6,516.
- Daily median: 988 events/day; peak days: Sep 6 (2,635), Sep 5 (2,186), Sep 1 (1,603).
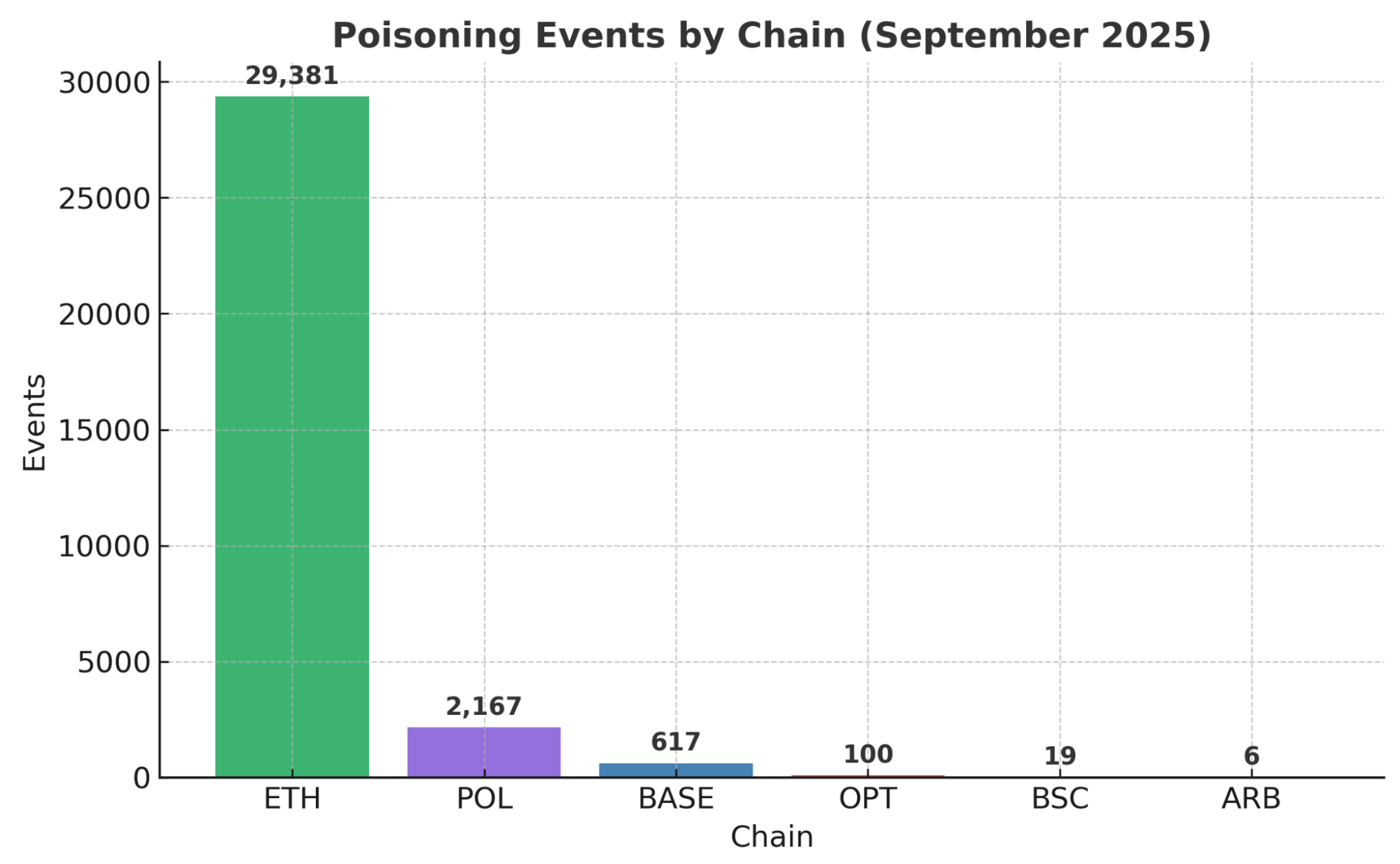
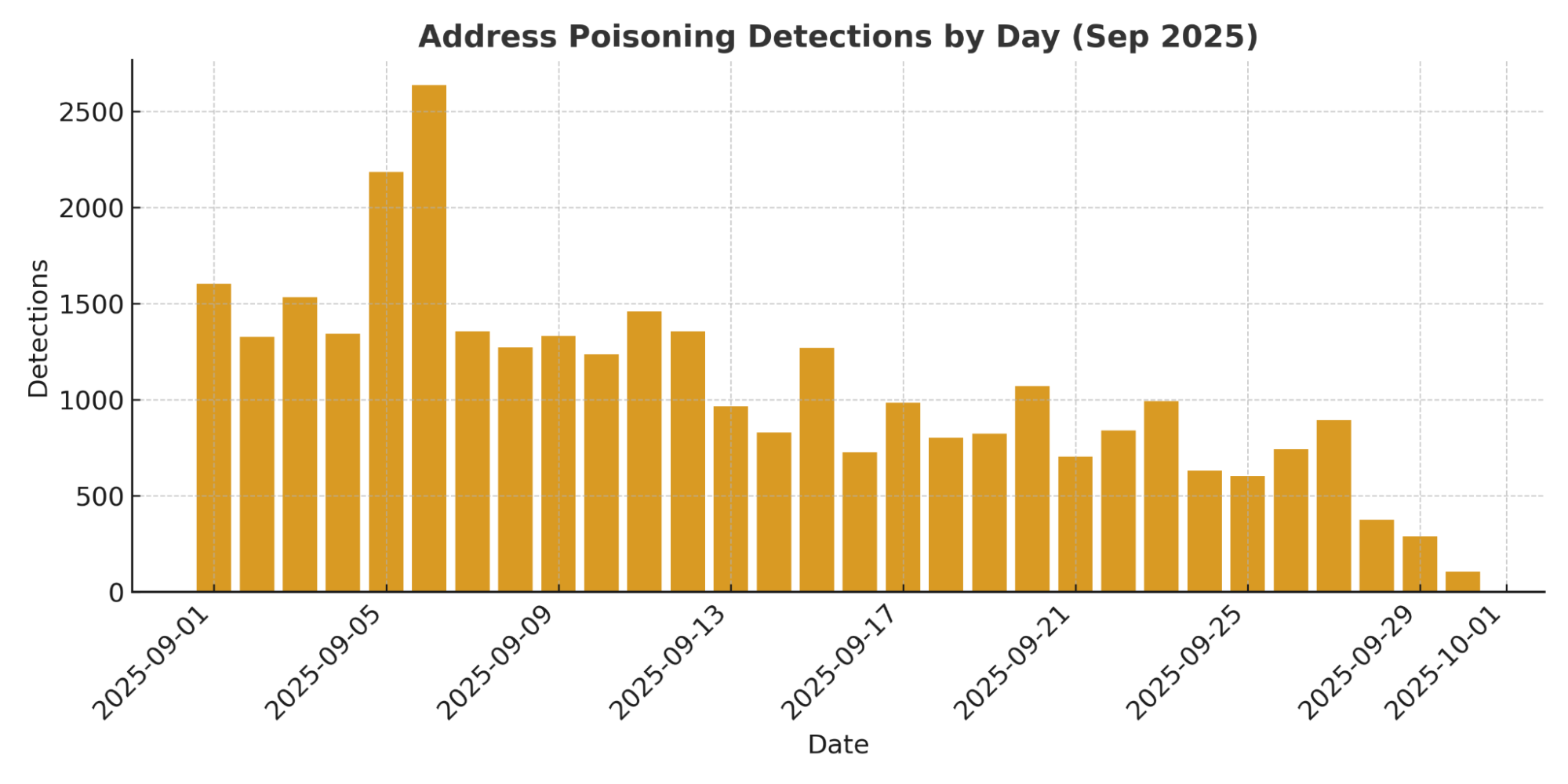
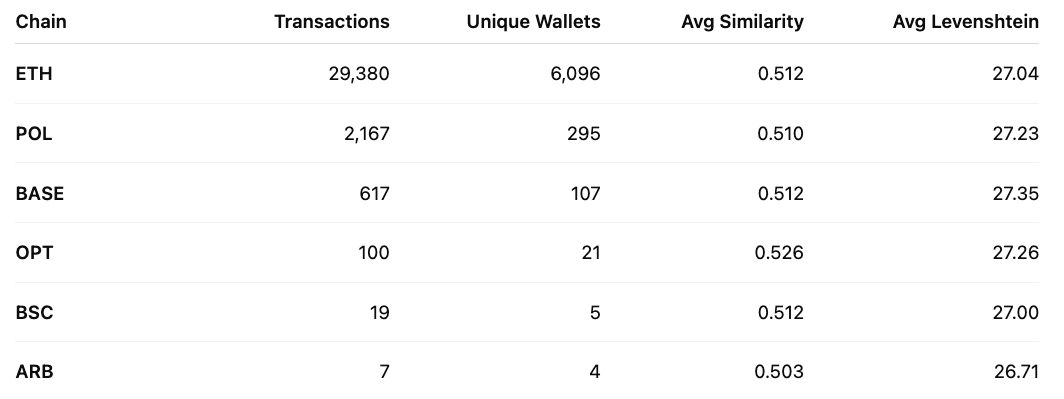
Ethereum remains the primary vector for poisoning attempts accounting for >90% of all flagged activity. What is also interesting is that Layer 2 networks (Polygon, Base, Optimism) are starting to show measurable activity, indicating scammers are adapting as more users move to L2 ecosystems.
Here are the top 5 stablecoin token symbol and number of transactions/victims:
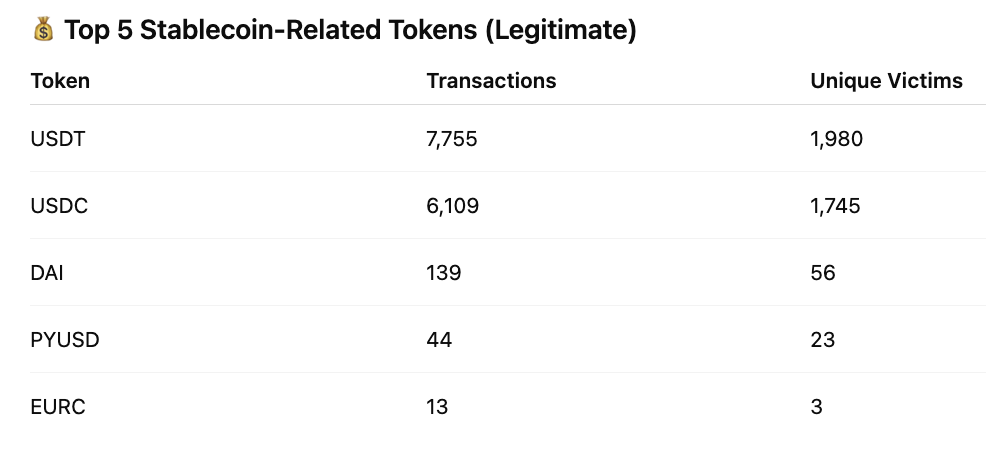
USDT and USDC Dominate Exposure:
Together, USDT and USDC account for 13,864 transactions, representing the majority of all observed activity. This concentration reflects their dominance in user holdings and transaction volume, making them prime targets for spoofing and address poisoning attacks. The high transaction counts suggest patterns of persistent or repeat victimization, potentially caused by repeated exposure to poisoned addresses or follow-up drain attempts. With nearly 2,000 unique USDT victims and 1,745 USDC victims, the data indicates broad exposure rather than isolated incidents. In contrast, tokens such as DAI (139 transactions) and PYUSD (44 transactions) show much lower volumes, likely due to their smaller user bases and limited exchange integration, while EURC remains minimally affected.
Stablecoin Spoofing:
Attackers also love to spoof the tokens and play with the linguistics of token names. In September, a majority of flagged incidents involved Unicode or visually confusing characters, subtle variations that survive copy-paste and evade naive string filters.
- Cyrillic homoglyphs (e.g. Latin “A” vs Cyrillic “А”) and Greek look-alikes dominate prefix-based spoofs.
- Zero-width joiners / invisible characters appear in 14% of spoofed “to” addresses, invisible to wallet UIs but critical in matching logic.
- Hybrid blends combine linguistic and truncation tactics (e.g., USDT₀ vs USDT0), blurring symbol and address spoofing.
Here are some of examples Top 10 spoofed stablecoins variants:
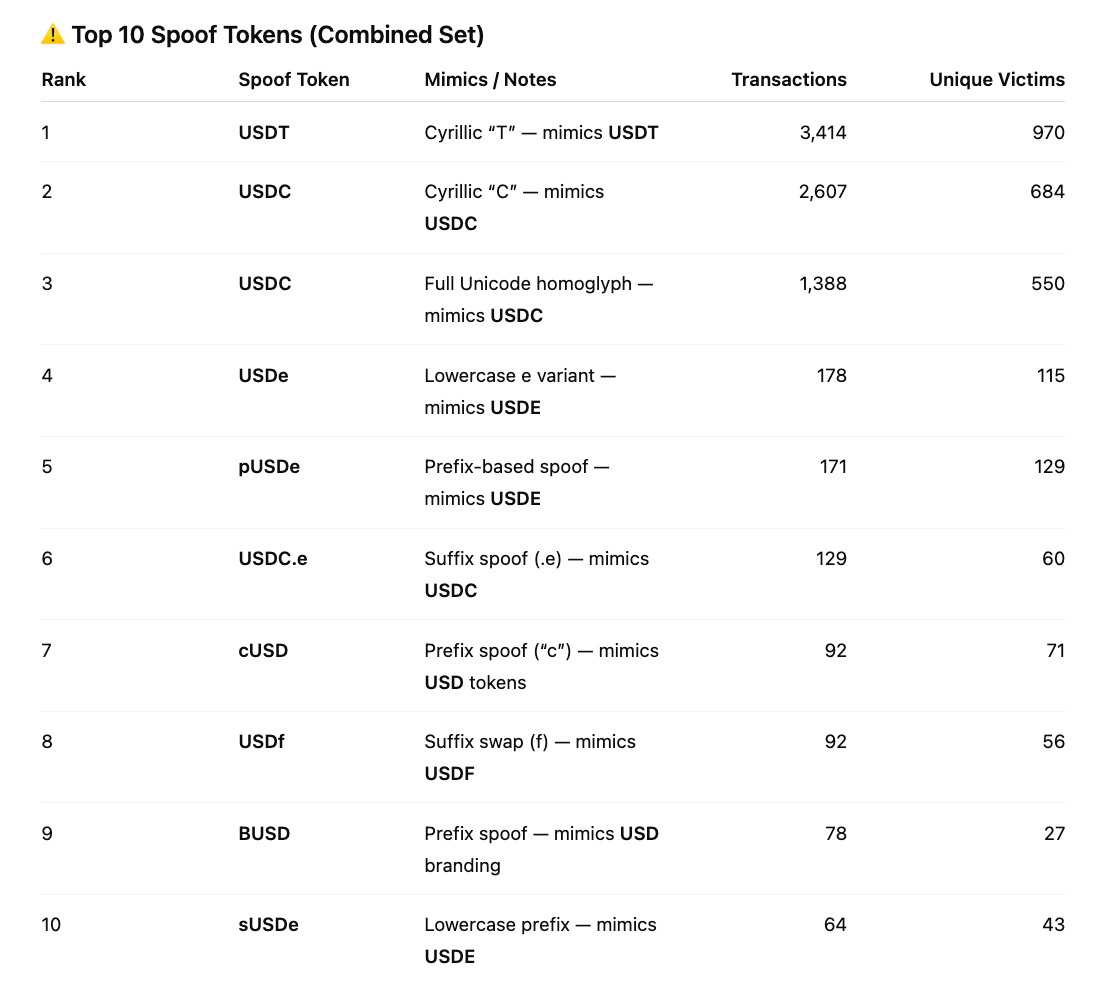
Incident Highlights:
In this section, we highlight several notable interesting incidents across different chains.
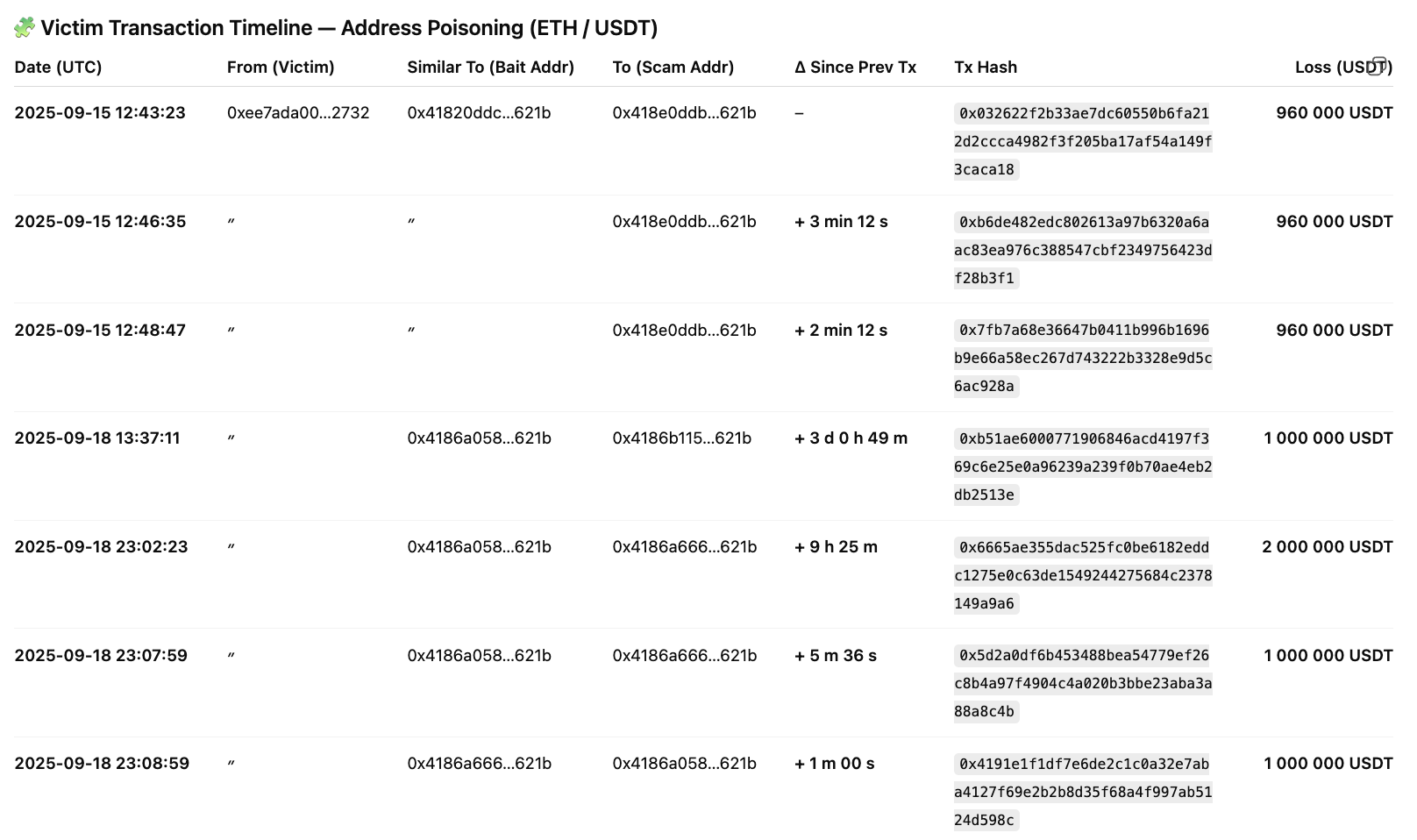
1) Ethereum — Large multi-burst drain (15 & 18 Sep 2025)
- Victim Address: 0xee7ada00c9e5f654c8f8ea0f355a1f3c50942732
- Incident type: Address-poisoning
- Total confirmed losses: ≈ 6,880,000 USDT.
- Distinct scam addresses observed: 4 — 0x418e0ddb…, 0x4186a058…, 0x4186a666…, 0x4186b115….
- Attack pattern: Two concentrated bursts of rapid, consecutive transfers (one on Sep 15, one on Sep 18).
- Time window (burst to burst): median gap ~3 minutes between consecutive transfers inside a burst; ~3 days between the two bursts.
Similarity / edit distance: string similarity 0.50–0.52; Levenshtein 25–28 (consistent with automated, small visual edits used to impersonate a known address).
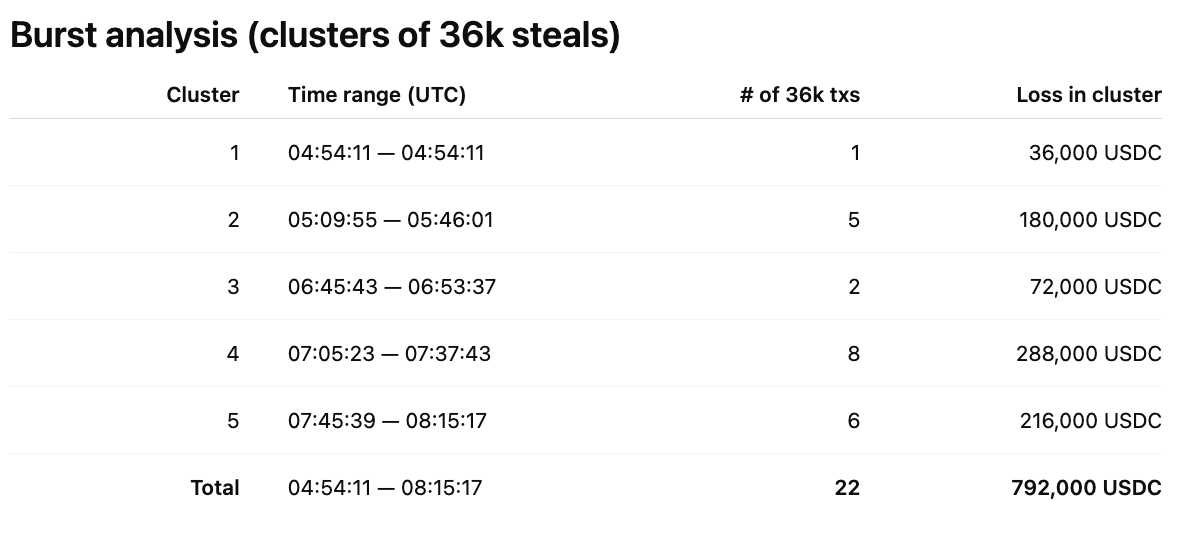
2) Polygon — Repeated 36k drains (02 Sep 2025)
- Victim address (repeated): 0x9d9c2ed2975c571befc58f359f45736cde75d90c
- Scam recipient: 0x9d9c2ed2975c571befc58f359f45736cde75d90c
- Time window: 2025-09-02 04:54:11 → 08:15:17 UTC (≈ 3 h 21 m).
- Confirmed 36,000 losses (events of 36k each): 22 transactions.
Total quantified loss (36k events): 22 × 36,000 = 792,000 USDC.
3) Base — Single large drain (24 Sep 2025)
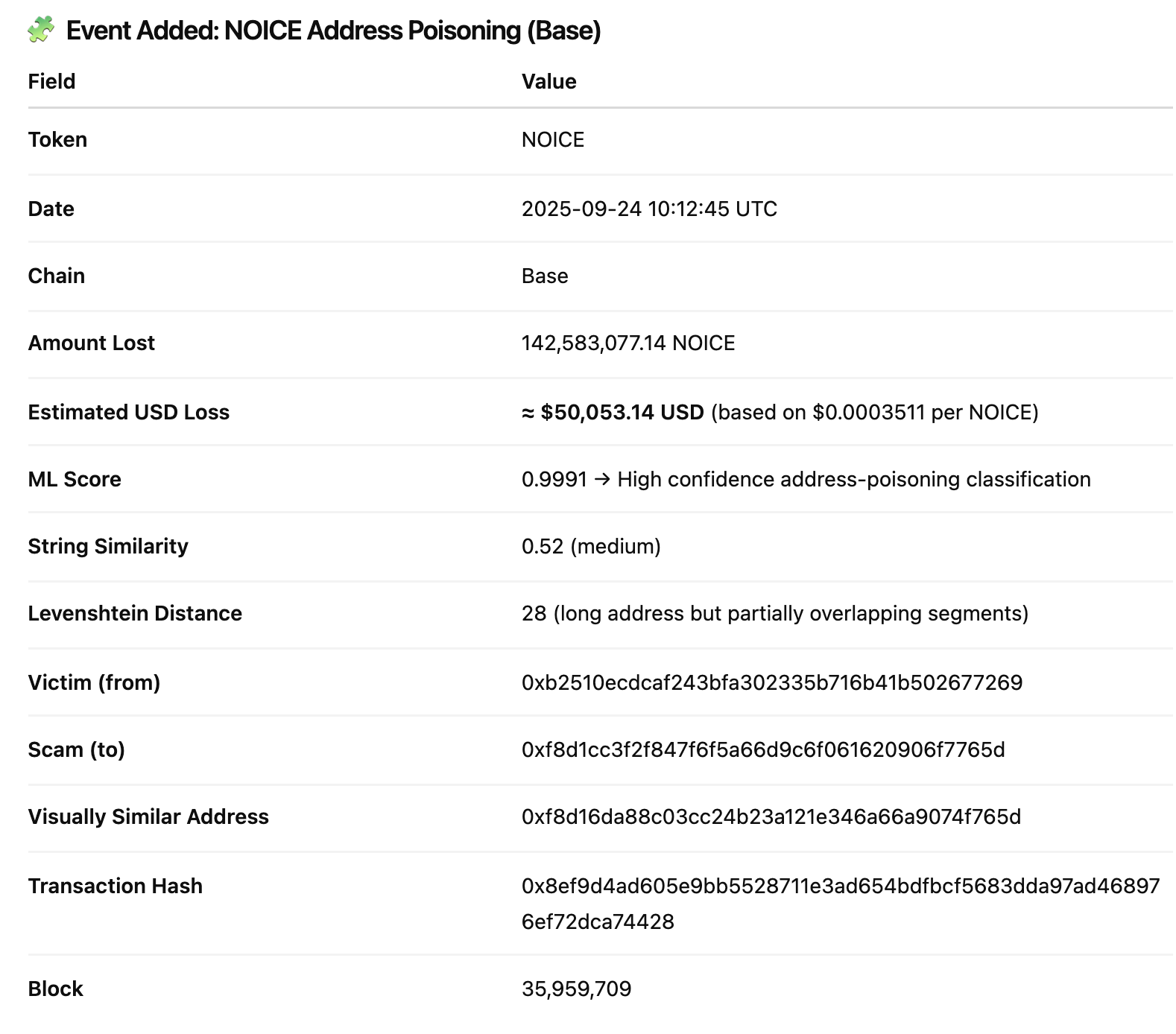
Single large drain vs repeated small drains: Unlike the previous incidents posts involving multi-transaction poisonings this incident is a single very large-loss event. The high ML score plus the near-identical spoofed address indicate the attacker prepared a visually-similar address aimed at fooling copy/paste or click-to-paste victims. The magnitude of the NOICE transfer suggests the victim copied a spoofed address (or selected it from a poisoned dropdown / UI), then executed a transfer, a classic address-poisoning outcome where large single transfers replace the multiple small-value patterns seen elsewhere.
Algorithm Refresher Overview: Here is an overview of the heuristics used in the algorithm we discussed previously. We’ve been improving its accuracy, which is now approaching 99%, and are focusing on extracting features related to visual spoofing and truncation, placing greater weight on prefix and postfix similarity measurements.
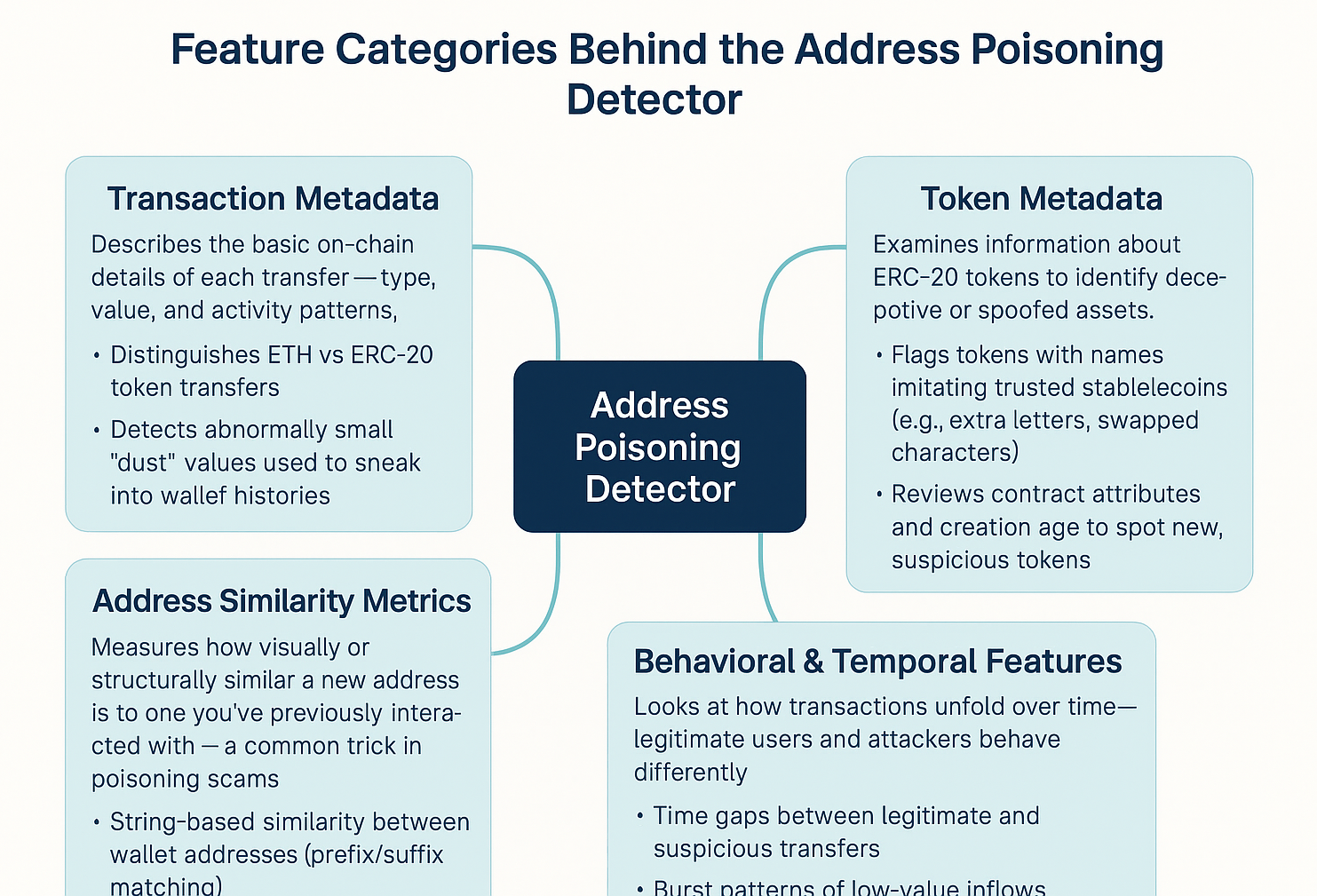
Model Training and Accuracy
Training Pipeline & Model Evaluation
Data: The model is trained on a labeled dataset combining real-world poisoning incidents with targeted synthetic samples to capture rare and emerging edge cases.
Model Search: Multiple candidate architectures are evaluated using cross-validation and hold-out wallet simulations designed to replicate real user flows.
Selection Criteria: The production model is chosen based on the optimal balance of ROC-AUC, precision–recall, and strict false-positive tolerance, prioritizing user trust over raw recall.
MLOps: Full model versioning and scheduled retraining enable rapid adaptation as adversaries evolve their tactics.
Current Performance: Accuracy is tracking toward ~99% under our evaluation protocol, with continuous monitoring to prevent model drift.
What This Means for Users and Security Partners
User Harm Focus: Webacy quantifies real victims and does deep investigation/verification on results and repeat targeting pattern beyond simple attacker noise. All of this is ingested by our real-time risk analysis engine and available through our APIs.
Campaign Detection: Clustering based on spoofed_to → similar_to relationships reveals which entities attackers are imitating and how concentrated each campaign is.
Operational Leverage: With near real-time scoring and versioned models, countermeasures can be deployed quickly as new attack strategies appear.
Call to Action: If you operate a wallet, exchange, or dApp, or touch stablecoins or any kind of digital assets, get in touch with us to proactively detect and mitigate risks.
